How To Install Chroot Bind On Centos Firewall
BIND Red Hat Customer Portal. The acl Access Control List statement allows you to define groups of hosts, so that they can be permitted or denied access to the nameserver. It takes the following form. The acl name statement name is the name of the access control list, and the match element option is usually an individual IP address such as 1. CIDR Classless Inter Domain Routing network notation for example, 1. For a list of already defined keywords, see Table 1. Predefined access control lists. How To Install Chroot Bind On Centos Firewall ConfigurationInstall and Configure CachingOnly DNS Server in RHEL. If youre looking to setup DNS CachingOnly Server in CentOSRHEL 6. In this howto article, we will walk you through the installation of a secure BIND9 authoritative DNS server on CentOS 6. BIND is open source software that. CentOS, Ubuntu, Fedora, Debian, Windows Server Server World OS CentOS 7 CentOS 6. In this tutorial, we will go over how to set up an internal DNS server, using the BIND name server software BIND9 on CentOS 7, that can be used by your Virtual. Install Setting Bind chroot for DNS ServerInstall Bind. Setup DNS server Bind chroot CentOS 6. CentOS 6BIND DNS Howtoing CentOS 6BIND DNS CentOS 6. Introduction. This is the ChrootBIND HOWTO see Where for the master site, which contains the latest copy. It is assumed that you already know how to configure. Hi Will i did the prefect server for centos 5. Install A Chrooted DNS Server BIND9 wont. Publisher 2007 Book Cover Template. Table 1. 7. 2. Predefined access control lists Keyword Description any Matches every IP address. Matches any IP address that is in use by the local system. Matches any IP address on any network to which the local system is connected. Does not match any IP address. The acl statement can be especially useful in conjunction with other statements such as options. Example 1. 7. 2, Using acl in conjunction with options defines two access control lists, black hats and red hats, and adds black hats on the blacklist while granting red hats a normal access. Example 1. 7. 2. Using acl in conjunction with optionsacl black hats. The options statement allows you to define global server configuration options as well as to set defaults for other statements. It can be used to specify the location of the named working directory, the types of queries allowed, and much more. It takes the following form. Table 1. 7. 3. Commonly used options Option Description allow query Specifies which hosts are allowed to query the nameserver for authoritative resource records. It accepts an access control list, a collection of IP addresses, or networks in the CIDR notation. All hosts are allowed by default. Specifies which hosts are allowed to query the nameserver for non authoritative data such as recursive queries. Only localhost and localnets are allowed by default. Specifies which hosts are not allowed to query the nameserver. How To Install Chroot Bind On Centos FirewalldEasy Guide on How to Configure BIND On Linux CentOSRHEL7 Learn how to configure Cachingonly. Easy Technical Guides for Windows and Linux. Install BIND. 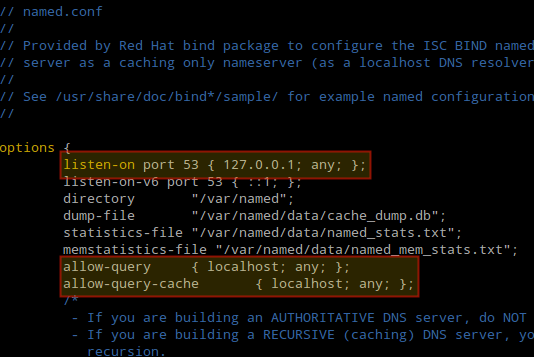 This option should be used when particular host or network floods the server with requests. The default option is none. Specifies a working directory for the named service. The default option is varnamed. Specifies whether to return DNSSEC related resource records. The default option is yes. Specifies whether to prove that resource records are authentic via DNSSEC. The default option is yes. Specifies a list of valid IP addresses for nameservers to which the requests should be forwarded for resolution. Specifies the behavior of the forwarders directive. It accepts the following options. The server will query the nameservers listed in the forwarders directive before attempting to resolve the name on its own. When unable to query the nameservers listed in the forwarders directive, the server will not attempt to resolve the name on its own. Specifies the IPv. On a DNS server that also acts as a gateway, you can use this option to answer queries originating from a single network only. All IPv. 4 interfaces are used by default. Specifies the IPv. On a DNS server that also acts as a gateway, you can use this option to answer queries originating from a single network only. All IPv. 6 interfaces are used by default. Specifies the maximum amount of memory to be used for server caches. When the limit is reached, the server causes records to expire prematurely so that the limit is not exceeded. In a server with multiple views, the limit applies separately to the cache of each view. The default option is 3. M. notify. Specifies whether to notify the secondary nameservers when a zone is updated. It accepts the following options. The server will notify all secondary nameservers. The server will not notify any secondary nameserver. The server will notify primary server for the zone only. The server will notify only the secondary servers that are specified in the also notify list within a zone statement. Specifies the location of the process ID file created by the named service. Specifies whether to act as a recursive server. The default option is yes. Specifies an alternate location for statistics files. The varnamednamed. To prevent distributed denial of service DDo. S attacks, it is recommended that you use the allow query cache option to restrict recursive DNS services for a particular subset of clients only. Example 1. 7. 4. Using the options statementoptions. M. directory varnamed. The zone statement allows you to define the characteristics of a zone, such as the location of its configuration file and zone specific options, and can be used to override the global options statements. It takes the following form. The zone name attribute is the name of the zone, zone class is the optional class of the zone, and option is a zone statement option as described in Table 1. Commonly used options. The zone name attribute is particularly important, as it is the default value assigned for the ORIGIN directive used within the corresponding zone file located in the varnamed directory. The named daemon appends the name of the zone to any non fully qualified domain name listed in the zone file. For example, if a zone statement defines the namespace for example. Table 1. 7. 4. Commonly used options Option Description allow query Specifies which clients are allowed to request information about this zone. This option overrides global allow query option. All query requests are allowed by default. Specifies which secondary servers are allowed to request a transfer of the zones information. All transfer requests are allowed by default. Specifies which hosts are allowed to dynamically update information in their zone. The default option is to deny all dynamic update requests. Note that you should be careful when allowing hosts to update information about their zone. Do not set IP addresses in this option unless the server is in the trusted network. Instead, use TSIG key as described in Section 1. Transaction SIGnatures TSIG. Specifies the name of the file in the named working directory that contains the zones configuration data. Specifies from which IP addresses to request authoritative zone information. This option is used only if the zone is defined as typeslave. Specifies whether to notify the secondary nameservers when a zone is updated. It accepts the following options. The server will notify all secondary nameservers. The server will not notify any secondary nameserver. The server will notify primary server for the zone only. The server will notify only the secondary servers that are specified in the also notify list within a zone statement. Specifies the zone type. It accepts the following options. Enforces the delegation status of infrastructure zones such as COM, NET, or ORG. Any answer that is received without an explicit or implicit delegation is treated as NXDOMAIN. This option is only applicable in TLDs Top Level Domain or root zone files used in recursive or caching implementations. Forwards all requests for information about this zone to other nameservers. A special type of zone used to point to the root nameservers which resolve queries when a zone is not otherwise known. No configuration beyond the default is necessary with a hint zone. Designates the nameserver as authoritative for this zone. A zone should be set as the master if the zones configuration files reside on the system. Designates the nameserver as a slave server for this zone. Master server is specified in masters directive. Most changes to the etcnamed. In Example 1. 7. 5, A zone statement for a primary nameserver, the zone is identified as example. How to Configure BIND On Linux RHELCent. OS 7. What is DNS In this Tutorial we are going to learn How to Configure BIND On Linux Cent. OSRHEL7 so lets first start with DNS. DNS Domain Name System is a hierarchical structure that is responsible for resolving hostnames into their numerical IP addresses for computer systems and vice versa. Domain Name System has been used on the internet and in the private networks as well. Type of DNS Servers. A Primary or Master DNS server has authority of its domain and it is maintainer of domains original zone data. Domain zone files are maintained on the Primary or Master DNS Server and they can propagate domains record to secondary servers. Secondary or Slave DNS Sever. A Secondary or Slave DNS server also has the authority of its domain and they stores domains zone data files as well but they just copied these files from primary DNS server. Whenever primary server made the update to domain zone files, the secondary server simply copy the updated file from primary server automatically. Secondary or Slave DNS servers are used to offloading the primary. Caching Only DNS Server. A Caching DNS Server doesnt have any authority for any domain. They just answer client queries after getting reply from Pimary or Secondary DNS servers. Caching servers are mostly used for redundancy, load sharing and provide faster response to the client queries. Caching Only DNS Server delivers data from the memory rather than from the disk. What is BIND in Linux BIND is short form of Berkeley Iinternet Name Domain which is implementation of DNS on Linux Operating System. It is one of the most popular and open source DNS application used by ISP Internet Service Providers and also by the private networks. RHEL7Cent. OS7 offers BIND as their default DNS software. In this giude we will configure Caching Only DNS Server and later in next coming articles we will install Primary and Slave DNS Servers. So for now lets install Caching Only DNS Server on RHEL7Cent. Os 7. If you are using Cent. OS 6. x, you should follow the below link. Required steps to install Caching Only DNS Server. Install BIND Package. Modify BIND configuration file etcnamed. Configure the SELinux context if enforcing mode. Enable BIND service at system startup. Start the BIND service. Allow DNS service port 5. Testing from client side. Step 1 Install BIND packagesyum install bind bind utils y. Step 2 Modify BIND Configuration File etcnamed. By default it works as a localhost DNS resolver only. Allow DNS to accept and answer client DNS queries from your local subnet edit named. Vi Text Editor and modify the following parameters according to your network settings. To verify configuration done in correct manners use the following commandnamed checkconf. Step 3 Configure the SELinux context if enforcing modesemanage fcontext a t namedconft etcnamed. Step 4 Enable BIND Service at System Startupsystemctl enable named. Step 5 Start BIND Servicesystemctl start named. To check statussystemctl status named. Step 6 Allow DNS Port 5. Linux Firewallfirewall cmd permanent add servicedns. Step 7 Testing From Client Side. For testing purpose we have one windows 7 client machine in our network. Before you start testing, make sure client ip settings is pointing our local caching only dns server as primary dns. In my test lab network DNS serve IP is 1. See result below How to Configure DNS BIND on RHEL7Cent.
This option should be used when particular host or network floods the server with requests. The default option is none. Specifies a working directory for the named service. The default option is varnamed. Specifies whether to return DNSSEC related resource records. The default option is yes. Specifies whether to prove that resource records are authentic via DNSSEC. The default option is yes. Specifies a list of valid IP addresses for nameservers to which the requests should be forwarded for resolution. Specifies the behavior of the forwarders directive. It accepts the following options. The server will query the nameservers listed in the forwarders directive before attempting to resolve the name on its own. When unable to query the nameservers listed in the forwarders directive, the server will not attempt to resolve the name on its own. Specifies the IPv. On a DNS server that also acts as a gateway, you can use this option to answer queries originating from a single network only. All IPv. 4 interfaces are used by default. Specifies the IPv. On a DNS server that also acts as a gateway, you can use this option to answer queries originating from a single network only. All IPv. 6 interfaces are used by default. Specifies the maximum amount of memory to be used for server caches. When the limit is reached, the server causes records to expire prematurely so that the limit is not exceeded. In a server with multiple views, the limit applies separately to the cache of each view. The default option is 3. M. notify. Specifies whether to notify the secondary nameservers when a zone is updated. It accepts the following options. The server will notify all secondary nameservers. The server will not notify any secondary nameserver. The server will notify primary server for the zone only. The server will notify only the secondary servers that are specified in the also notify list within a zone statement. Specifies the location of the process ID file created by the named service. Specifies whether to act as a recursive server. The default option is yes. Specifies an alternate location for statistics files. The varnamednamed. To prevent distributed denial of service DDo. S attacks, it is recommended that you use the allow query cache option to restrict recursive DNS services for a particular subset of clients only. Example 1. 7. 4. Using the options statementoptions. M. directory varnamed. The zone statement allows you to define the characteristics of a zone, such as the location of its configuration file and zone specific options, and can be used to override the global options statements. It takes the following form. The zone name attribute is the name of the zone, zone class is the optional class of the zone, and option is a zone statement option as described in Table 1. Commonly used options. The zone name attribute is particularly important, as it is the default value assigned for the ORIGIN directive used within the corresponding zone file located in the varnamed directory. The named daemon appends the name of the zone to any non fully qualified domain name listed in the zone file. For example, if a zone statement defines the namespace for example. Table 1. 7. 4. Commonly used options Option Description allow query Specifies which clients are allowed to request information about this zone. This option overrides global allow query option. All query requests are allowed by default. Specifies which secondary servers are allowed to request a transfer of the zones information. All transfer requests are allowed by default. Specifies which hosts are allowed to dynamically update information in their zone. The default option is to deny all dynamic update requests. Note that you should be careful when allowing hosts to update information about their zone. Do not set IP addresses in this option unless the server is in the trusted network. Instead, use TSIG key as described in Section 1. Transaction SIGnatures TSIG. Specifies the name of the file in the named working directory that contains the zones configuration data. Specifies from which IP addresses to request authoritative zone information. This option is used only if the zone is defined as typeslave. Specifies whether to notify the secondary nameservers when a zone is updated. It accepts the following options. The server will notify all secondary nameservers. The server will not notify any secondary nameserver. The server will notify primary server for the zone only. The server will notify only the secondary servers that are specified in the also notify list within a zone statement. Specifies the zone type. It accepts the following options. Enforces the delegation status of infrastructure zones such as COM, NET, or ORG. Any answer that is received without an explicit or implicit delegation is treated as NXDOMAIN. This option is only applicable in TLDs Top Level Domain or root zone files used in recursive or caching implementations. Forwards all requests for information about this zone to other nameservers. A special type of zone used to point to the root nameservers which resolve queries when a zone is not otherwise known. No configuration beyond the default is necessary with a hint zone. Designates the nameserver as authoritative for this zone. A zone should be set as the master if the zones configuration files reside on the system. Designates the nameserver as a slave server for this zone. Master server is specified in masters directive. Most changes to the etcnamed. In Example 1. 7. 5, A zone statement for a primary nameserver, the zone is identified as example. How to Configure BIND On Linux RHELCent. OS 7. What is DNS In this Tutorial we are going to learn How to Configure BIND On Linux Cent. OSRHEL7 so lets first start with DNS. DNS Domain Name System is a hierarchical structure that is responsible for resolving hostnames into their numerical IP addresses for computer systems and vice versa. Domain Name System has been used on the internet and in the private networks as well. Type of DNS Servers. A Primary or Master DNS server has authority of its domain and it is maintainer of domains original zone data. Domain zone files are maintained on the Primary or Master DNS Server and they can propagate domains record to secondary servers. Secondary or Slave DNS Sever. A Secondary or Slave DNS server also has the authority of its domain and they stores domains zone data files as well but they just copied these files from primary DNS server. Whenever primary server made the update to domain zone files, the secondary server simply copy the updated file from primary server automatically. Secondary or Slave DNS servers are used to offloading the primary. Caching Only DNS Server. A Caching DNS Server doesnt have any authority for any domain. They just answer client queries after getting reply from Pimary or Secondary DNS servers. Caching servers are mostly used for redundancy, load sharing and provide faster response to the client queries. Caching Only DNS Server delivers data from the memory rather than from the disk. What is BIND in Linux BIND is short form of Berkeley Iinternet Name Domain which is implementation of DNS on Linux Operating System. It is one of the most popular and open source DNS application used by ISP Internet Service Providers and also by the private networks. RHEL7Cent. OS7 offers BIND as their default DNS software. In this giude we will configure Caching Only DNS Server and later in next coming articles we will install Primary and Slave DNS Servers. So for now lets install Caching Only DNS Server on RHEL7Cent. Os 7. If you are using Cent. OS 6. x, you should follow the below link. Required steps to install Caching Only DNS Server. Install BIND Package. Modify BIND configuration file etcnamed. Configure the SELinux context if enforcing mode. Enable BIND service at system startup. Start the BIND service. Allow DNS service port 5. Testing from client side. Step 1 Install BIND packagesyum install bind bind utils y. Step 2 Modify BIND Configuration File etcnamed. By default it works as a localhost DNS resolver only. Allow DNS to accept and answer client DNS queries from your local subnet edit named. Vi Text Editor and modify the following parameters according to your network settings. To verify configuration done in correct manners use the following commandnamed checkconf. Step 3 Configure the SELinux context if enforcing modesemanage fcontext a t namedconft etcnamed. Step 4 Enable BIND Service at System Startupsystemctl enable named. Step 5 Start BIND Servicesystemctl start named. To check statussystemctl status named. Step 6 Allow DNS Port 5. Linux Firewallfirewall cmd permanent add servicedns. Step 7 Testing From Client Side. For testing purpose we have one windows 7 client machine in our network. Before you start testing, make sure client ip settings is pointing our local caching only dns server as primary dns. In my test lab network DNS serve IP is 1. See result below How to Configure DNS BIND on RHEL7Cent.